>Please check here for the first report.
>Please check here for the second report.
>Please check here for the third report.
SB Technology (hereinafter referred to as "our company") has announced that an unauthorized relay (hereinafter referred to as "hereinafter referred to as this") occurred due to a failure to change the settings during troubleshooting maintenance that occurred on March 18, 2022 in the email relay system of the local Local Government Information Security Cloud that we built and managed. We have implemented measures to prevent recurrence. We would like to inform you that we are now able to report on the current situation and the specific implementation status of the measures we are currently implementing to prevent recurrence.
We deeply apologize for the great concern and inconvenience this incident has caused to our customers and other stakeholders.
1. Current status report
We have continued to monitor the following three points, but there has been no recurrence of events caused by this event.
① Regarding the situation where unauthorized relay is possible
The issue was resolved by fixing the incorrect setting change at 18:55 on March 18th. Since then, there have been no recurrences of unauthorized relay mails being sent by third parties or situations where unauthorized relay is possible.
②About reporting damage caused by fraudulent email sending
A fraudulent email was sent due to an incorrect emergency maintenance setting at 15:58 on March 18th, but as of today, we have not received any reports of damage.
③ Regarding registration of reception rejection list
At 20:07 on March 20th, we confirmed that the main rejection list had been removed, and it is now possible to send emails to the email addresses necessary for work. Since then, we have not confirmed any email interruptions due to registration on the rejection list that occurred on March 18th.
2. cause
When maintenance was carried out on the ACL (list for controlling communications) in the email relay system, there was a flaw in this setting, which allowed unauthorized relaying.
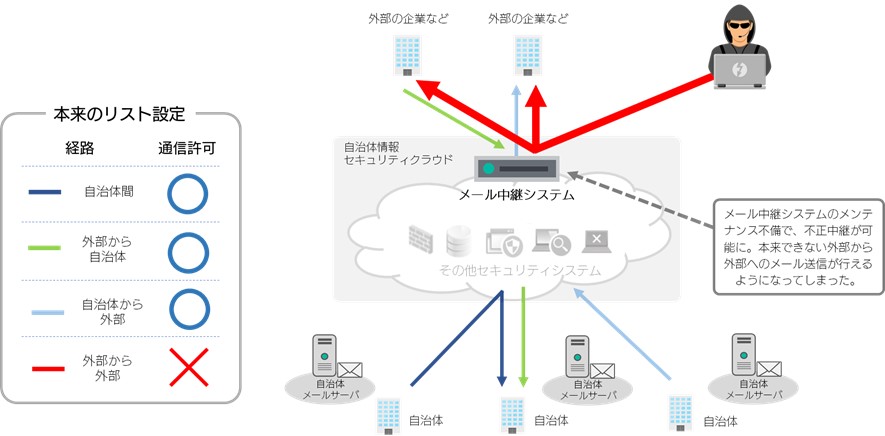
Normally, when changing and activating settings, the operator who made the settings and another person are supposed to double-check that there are no problems with the changes. However, during this emergency maintenance, the double checks were insufficient, allowing unauthorized relaying.
Additionally, we were unable to detect the issue early because we did not conduct any unauthorized relay tests after changing the settings.
3. Regarding recurrence prevention measures
Since the occurrence of this incident, we have carried out thorough double checks and monitored unauthorized relays using check tools. Specifically, we are taking the following measures to prevent recurrence.
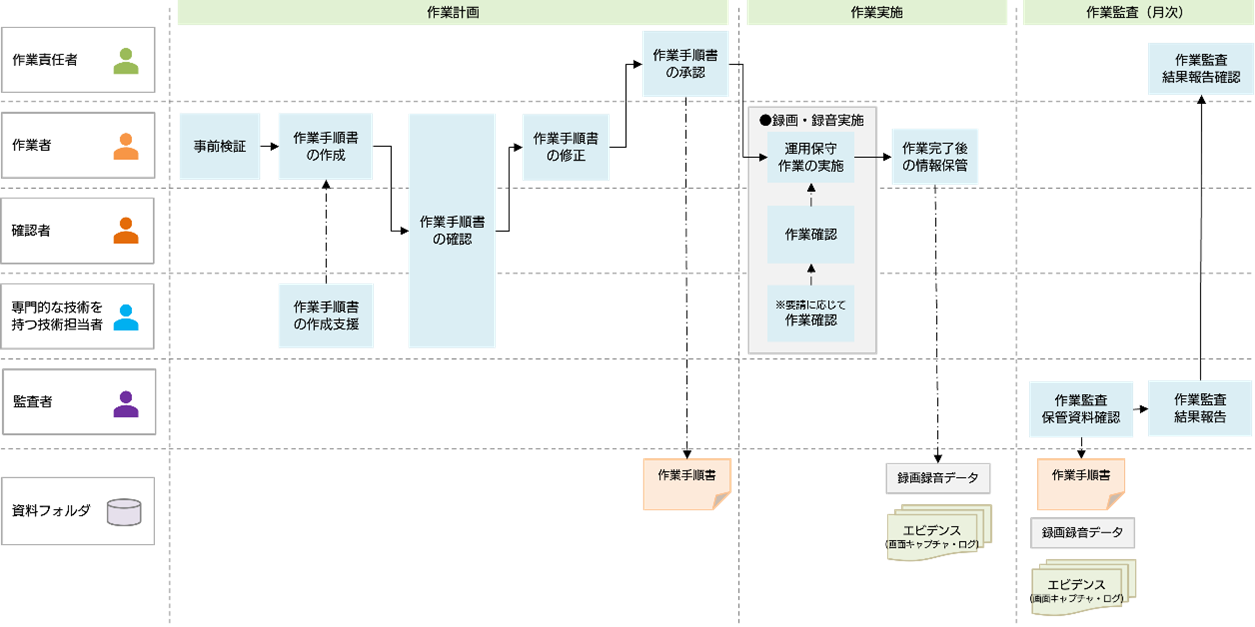
・Thorough double-checking
<Normal flow>
Based on the operation and maintenance work management procedures, when handling operation and maintenance work for equipment and services, it is always carried out by a team of two people: an operator and a checker. Depending on the content of the work to be carried out, a person with specialized skills may be required to attend the work (the necessity of a specialist will be determined at the time of creating the work procedure manual). The work will be carried out in accordance with the work procedure manual prepared in advance, and the work will be carried out after the worker and the person confirming the work have read the details together before starting the work.
During the work, the work screen is shared and confirmation is performed by pointing and calling out. The operation screen and audio will be recorded and saved as evidence. The person confirming that work procedures are being carried out in accordance with the manual and that evidence is being preserved. After completing the work, the worker submits information such as video/recording data to the designated folder.
In order to ensure that these tasks are being carried out in accordance with the procedures, an auditor will conduct an audit of the progress of the tasks. The auditor conducts an audit based on the stored information and reports the work audit results to the person in charge of the work.
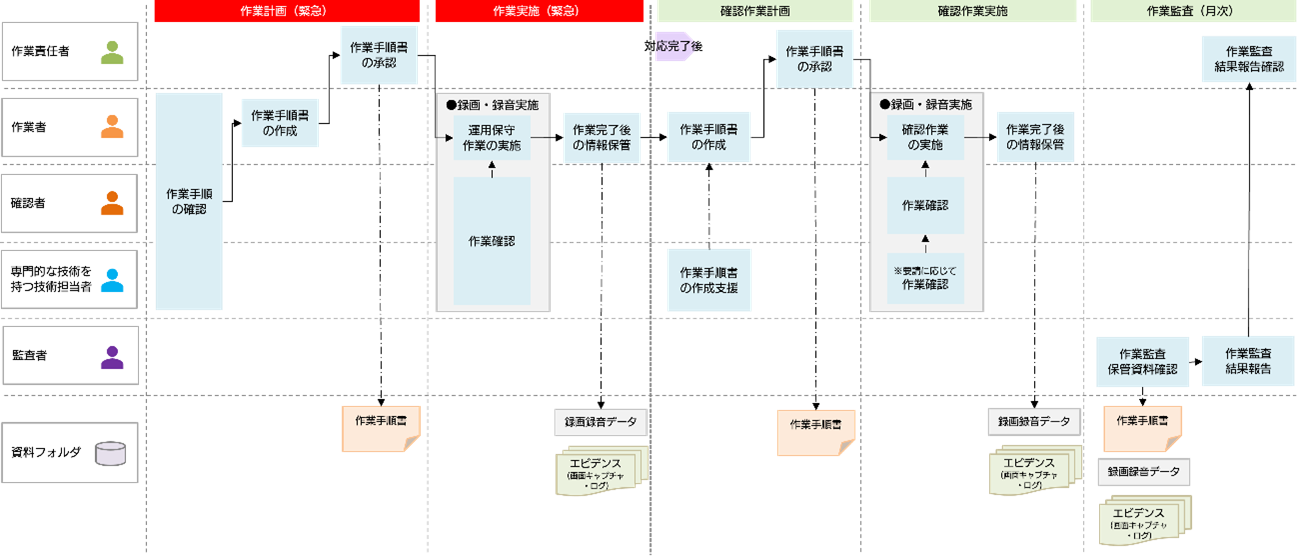
<Emergency flow>
When emergency work is required, such as when a failure occurs, we shorten the creation of work procedure manuals and prioritize recovery efforts in the presence of specialists with specialized skills. The content of the work is confirmed by the worker, the confirmer, and the person in charge with specialized skills, and a work procedure manual is created for the content of the work.
After the troubleshooting is complete, we will check again to see if there are any abnormalities in the settings that were changed during the troubleshooting or in the operation after the settings have been changed. For confirmation work, we will create a work procedure manual in advance and carry out the work according to the work procedure manual.
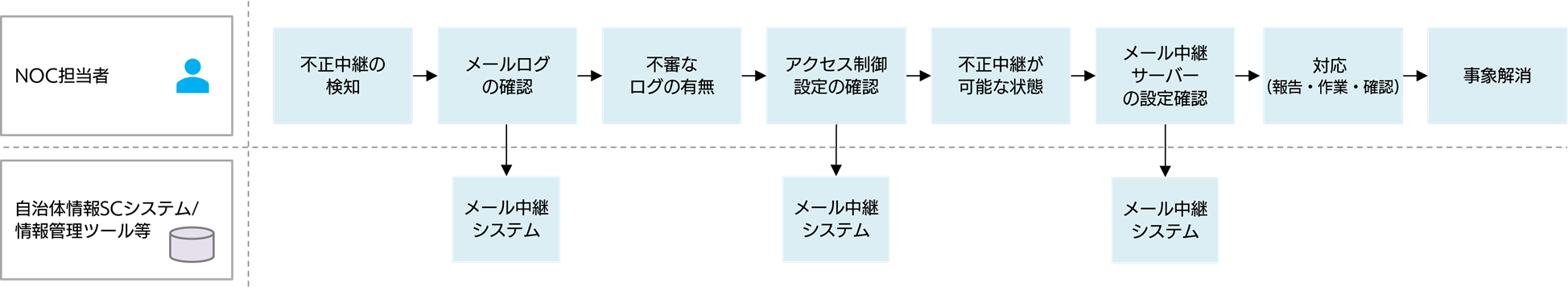
・Unauthorized relay monitoring using check tools
We monitor the email relay system at regular intervals using an unauthorized relay check tool. If we detect that unauthorized relaying is possible, our NOC (Network Operation Center) will respond immediately 24 hours a day, 365 days a year.
We will continue to work to improve quality so that our customers can use our services with peace of mind.
Contact information regarding this matter
● SB Technology Corp. Corporate Communication Group Yoshida, Baba
E-mail: sbt-pr@tech.softbank.co.jp
Tel: 03-6892-3063 (Weekdays 9:00-17:45)