>Please check here for the second report.
>Please check here for the third report.
>Please check here for the final report.
SB Technology (hereinafter referred to as the Company) has discovered that the mail relay system of Local Government Information Security Cloud, which the Company built and manages, has become in a state where unauthorized relaying (open relay) is possible due to an incorrect setting change during troubleshooting maintenance. We have confirmed that the email was used by three parties to send emails. This resulted in a large number of emails being sent, resulting in the email being registered on the reject list and being unable to send emails from each local government. In response to this, after we resolved the situation where unauthorized relaying was possible, we applied for cancellation to each organization that manages the rejection list, and at 20:07 on March 20th, we confirmed that the main rejection list had been lifted. .
Additionally, the total number of fraudulently sent emails was 912,299, of which 2,467 were for domestic domains (.jp) and 909,832 were for foreign domains (others).
We deeply apologize for the great concern and inconvenience this has caused to our customers and many other stakeholders.
We are currently continuing to investigate and respond, but we have not confirmed that information within each local government, including personal information, was leaked as a result of this incident.
A summary of the confirmed facts is as follows.
1. History of response
| Friday, March 18th | 14:43 | A transmission failure occurred in the mail relay system. |
|---|---|---|
| 14:50 | An investigation has begun to determine the cause of the transmission failure. | |
| 15:58 | We performed emergency maintenance of the communication control list (hereinafter referred to as ACL) and resolved the transmission failure. | |
| 18:40 | Detected an abnormality in the email relay system and began an investigation. As a result of the investigation, it was found that there were deficiencies in the content of the 15:58 event, and ① it was found that unauthorized relaying was possible. |
|
| 18:55 | Corrected the defect and ① resolved the unauthorized relay status. | |
| 21:30 | Confirm that the email relay system is registered in the ② Reject Reception List. Start of measures for cancellation. | |
| Saturday, March 19th | 19:00~ | Through log analysis, we confirmed the local government where the unauthorized relay occurred, the number of unauthorized emails sent, and the time of transmission. Reports will be made to prefectural officials one by one. |
| Sunday, March 20th | 20:07 | ② Confirm that the major list of rejected recipients has been removed. It is now possible to send to e-mail addresses that are necessary for business purposes and that were previously unavailable. |
| Monday, March 21st | 18:00~ | Report the total number of fraudulently sent emails and the number of emails sent to domestic domains (.jp) to the person in charge of each prefecture. |
2. cause
We performed ACL maintenance on the email relay system, but there was a flaw in this setting, which made unauthorized relay possible.
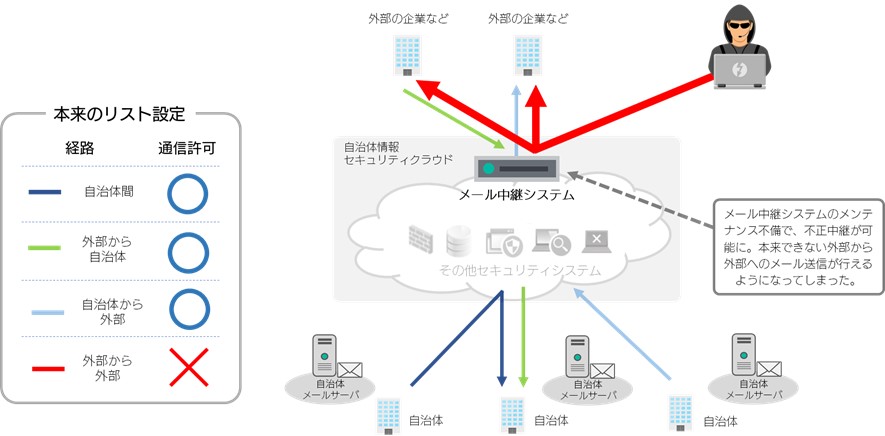
Normally, when changing and activating settings, a person other than the person who made the settings should double-check that the changes are correct. However, during this emergency maintenance, the double checks were insufficient, allowing unauthorized relaying.
Additionally, we were unable to detect the issue early because we did not conduct any unauthorized relay tests after changing the settings.
3. Impact range
(1) Number of emails sent by unauthorized relay: 912,299
(2) Email address believed to have been used for unauthorized relay
It is believed that the email was used from an email address available on the Internet.
(3) A situation occurred where some emails could not be sent.
When changing the settings of the email relay system managed by our company, there was a flaw that made it possible for unauthorized relaying, which was used by a malicious third party to send email. As a result, a large number of emails were sent, and as a result, the email was registered on the reject list, resulting in the inability to send some emails from local governments.
4. Measures to prevent recurrence
・Double check
Record work details for thorough double-checking. During work, the settings are read out loud and recorded in audio and video. We also have a third party to check the recorded data to ensure that double checks are carried out. Incorporate these into your operational rules.
・Unauthorized relay check
In addition to checking the settings, we will conduct a thorough inspection using a separate unauthorized relay check tool.
In the future, we will strive to thoroughly implement measures to prevent recurrence to prevent such situations from occurring.
Contact information regarding this matter
● SB Technology Corp. Corporate Communication Group Yoshida, Baba
E-mail: sbt-pr@tech.softbank.co.jp